on
Security
Tokopedia Persisted XSS Vulnerability
This is a documentation of a persisted XSS vulnerability in Tokopedia, an Indonesian e-commerce startup.
Timeline
December 12, 2016: A report is made to Tokopedia regarding the vulnerability in the morning. security analyst responded that Tokopedia has received a report from December 10, 2016 regarding the issue. So it’s a duplicate report.
December 13, 2016: The patch is deployed.
The Vulnerability
The vulnerability existed on Tokopedia’s search keyword autocomplete system.
To exploit the vulnerability, insert JavaScript as a search keyword with <script> tag.
<script>alert('tes')</script>
The following screenshot shows the search bar, with the payload inserted.
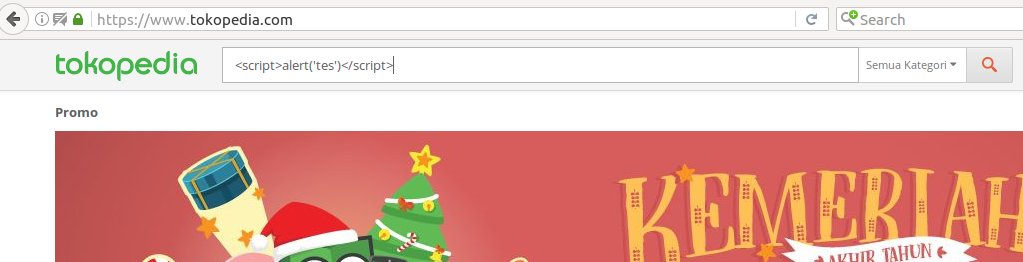
After the form is submitted, the injected JavaScript isn’t executed right away.
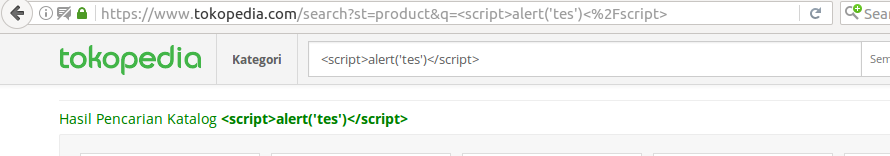
It’s going to be executed when the user clears the search bar. The search bar will then try to show the list of keywords the user has used in their searches. This is where the JavaScript is going to be executed.
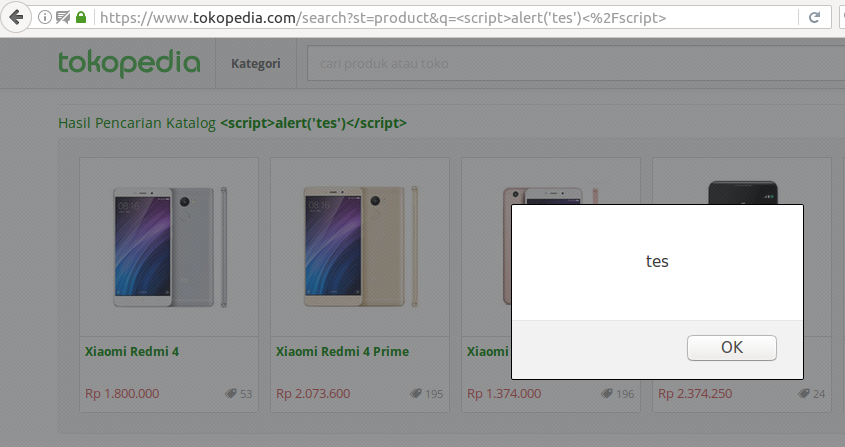
Even after moving to another page, the JavaScript will keep being executed everytime the search autocomplete tries to show the search history of the user.
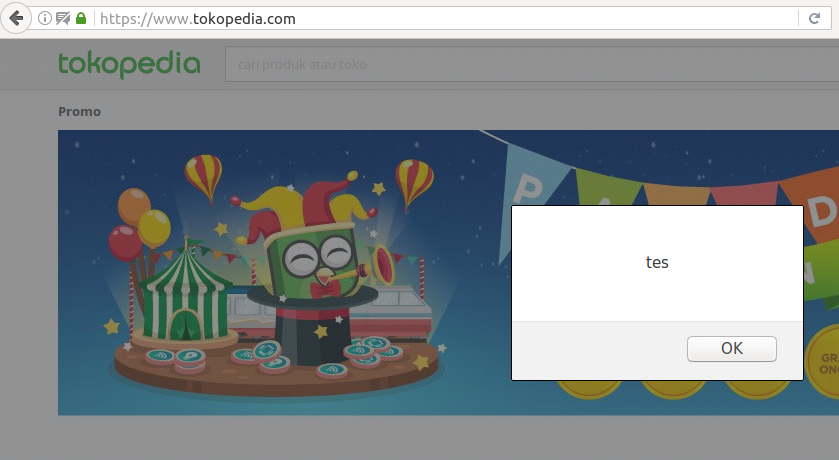
Since the search form is submitted using HTTP GET request, the attacker can simply send a link containing the payload to the victim.
https://www.tokopedia.com/search?st=product&q=%3Cscript%3Ealert%28%27tes%27%29%3C%2Fscript%3E
Risks
XSS is a common problem, and it is among the vulnerabilities listed on OWASP.
By enabling users to inject JavaScript to our web page, we’re enabling attackers to run arbitrary JavaScript on our users’ browser. Technically, the attackers can control and access anything that the browser allows them to.
The worst part of this XSS vulnerability is the fact that the JavaScript injected by the attacker can be run in every page that renders the search bar. Once the attacker injected the malicious JavaScript to the victim’s search history, Tokopedia will run the malicious JavaScript everytime the search history is rendered until the victim’s searched enough keywords to exclude the malicious payload from the search history.