on
Security
Jualo User Bio XSS
This is a documentation of an XSS vulnerability in Jualo, another Indonesian e-commerce startup.
Timeline
October 17, 2015: A report is made to Jualo regarding the vulnerability around noon.
October 20, 2015: No reply from Jualo since the report was sent, so I kept checking if the bug is still around. When checking on the morning on October 20, the bug is already fixed.
The Vulnerability
Since I was a bit bored on the weekend, I decided to go to Jualo and try checking for web vulnerabilities. I created an account and uploaded a product.
I tried putting HTML brackets in the product’s name and description, and inspecting the element where the product name and description is rendered on the browser. But the HTML brackets are properly encoded, so it doesn’t render any HTML elements.
Then, I moved on to the user profile page, and see the menu to edit the profile.
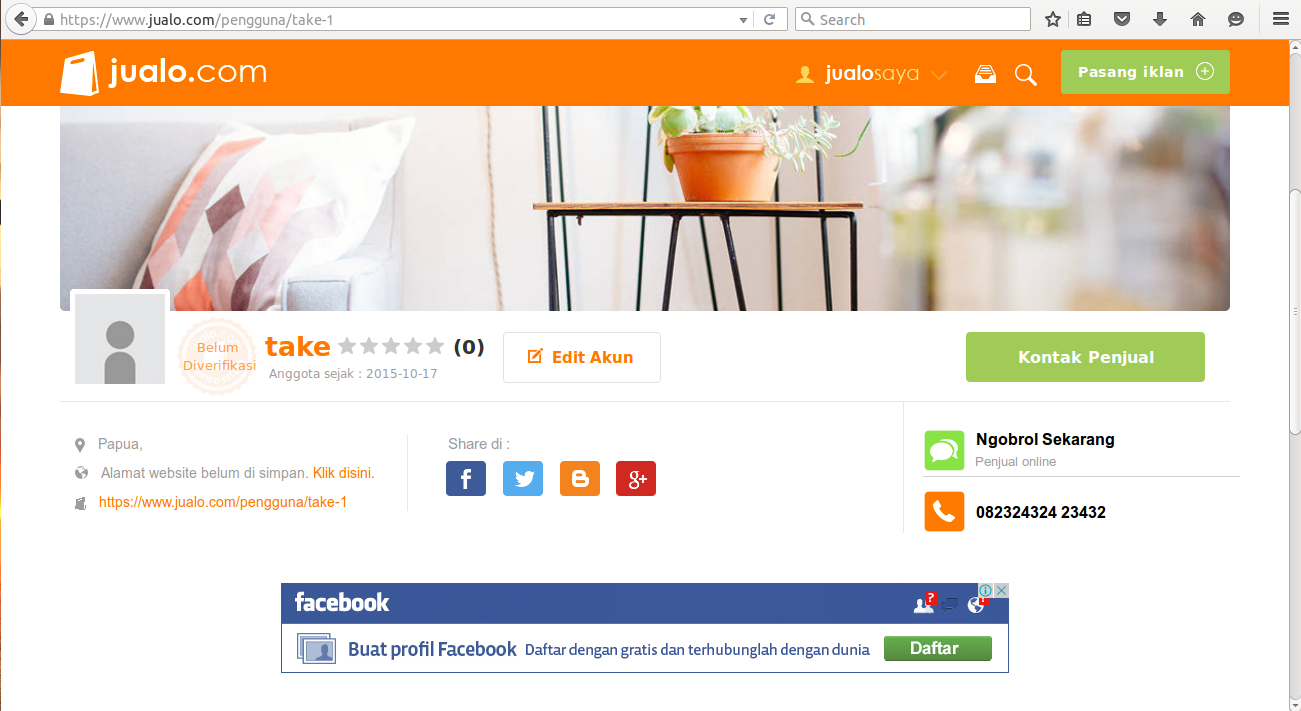
I played a bit with the fields available for editing the user information by inserting HTML tags and brackets, and see how it’s rendered in the page. I found out that the brackets and HTML characters I inputted to the user bio field are rendered as they are in the page when inspecting the elements.
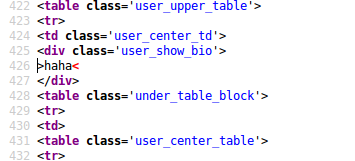
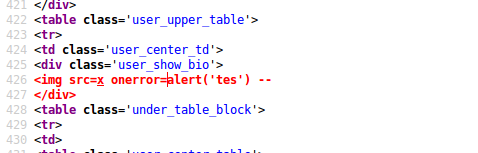
The problem is that whenever I put a full HTML tag (for example, <script> and </script>), it is filtered by Jualo. So I decided to put this string to override the closing </div> tag.
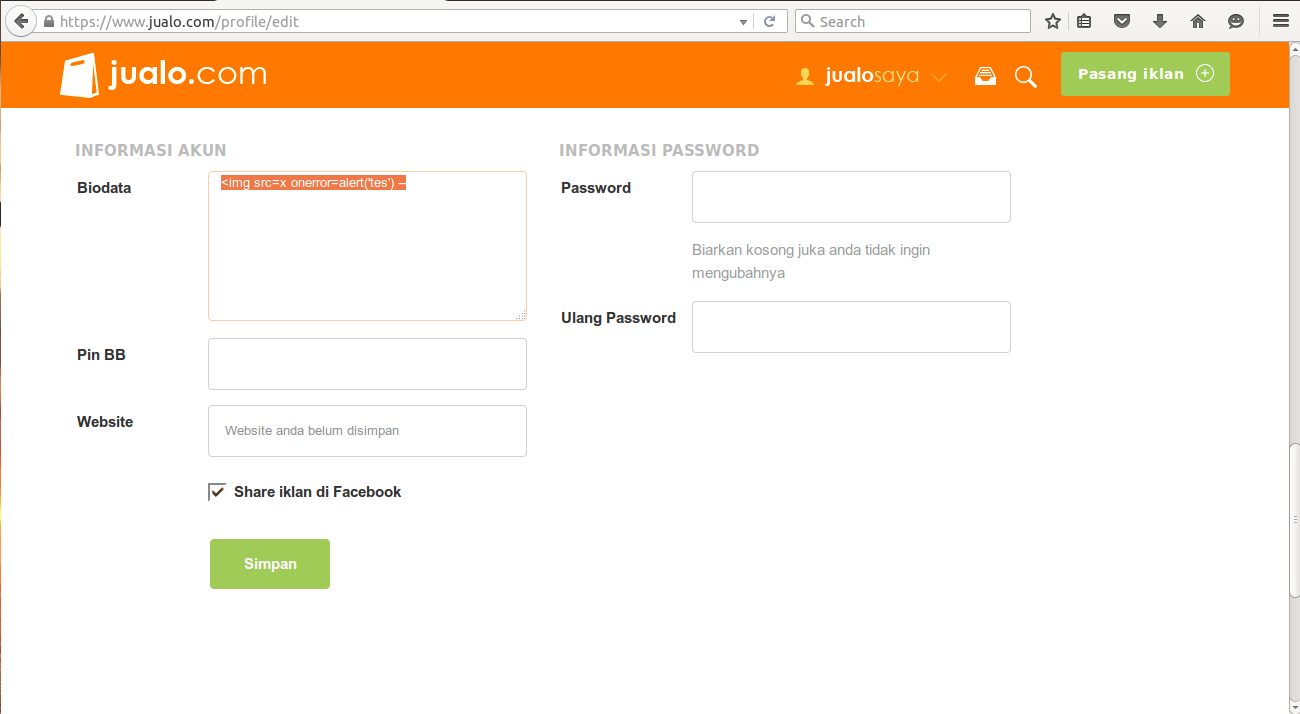
Let’s zoom it in.
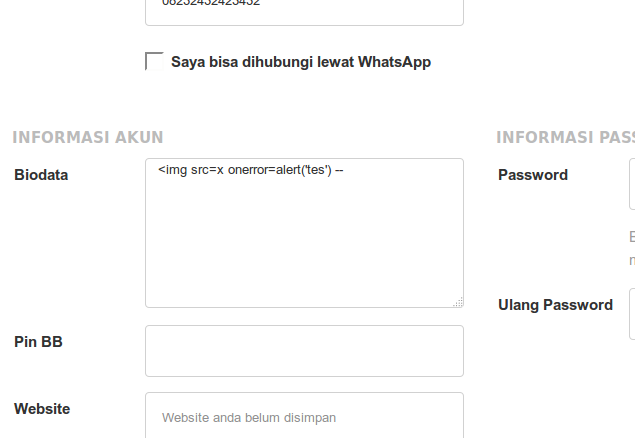
After I saved the new bio with that string, whenever I opened the user’s profile (either logged in or not) I’ll get this alert.
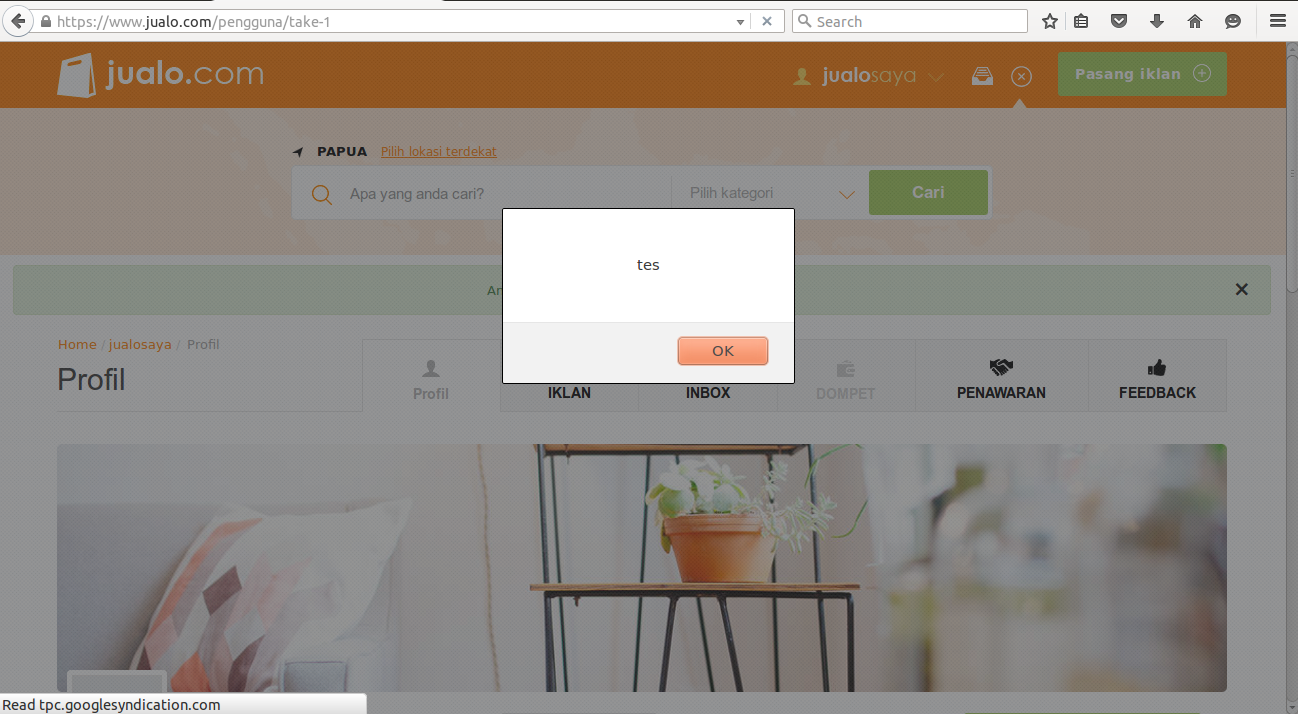
If we inspect the element, we can see that the closing </div> tag is overridden by the tag I put in the bio.
Risks
XSS is a common vulnerability, and OWASP has a pretty good overview regarding XSS and the risks. XSS enables attackers to modify a web page’s display at will and run malicious scripts in the client’s browser.